You might have heard about cyber-attacks and their impact on victims. Data breaches can devastate organizations, from halting business operations to paying massive amounts as ransom. Companies aren’t the sole target of cybercriminals. Schools, banks, hospitals, and others aren’t left out. Fortunately, data security can keep your organization safe from hackers.
Is Data Security Important?
Data is a valuable asset in all fields of an economy. Your stored data faces numerous potential risks. A user may mistakenly overwrite or delete sensitive files. Besides, a computer virus may corrupt your data, or it may get lost if your system fails. Hackers can alter or delete it, and it can get into the wrong hand if devices like smartphones get missing.
Protecting your data from theft, unauthorized access, or corruption is necessary. Data security refers to every approach used in keeping digital information safe. It can be physical protection of storage devices or hardware, logical defense for software applications, or administrative and access controls.
Also, data protection involves specific processes and organizational policies. You will have robust data security when you correctly apply these strategies. As a result, your digital information will be safe from cybercriminal activities. Data protection solutions also safeguard sensitive data from human error and insider threats. The pair is among the significant causes of data breaches.
How Data Security Secures Sensitive Data
Data security uses technologies and tools to apply various protections to sensitive data. It gives organizations more visibility on the storage of their digital information and its usage. Besides, it automates reports for audits in compliance with regulatory requirements.
Common Ways Of Securing Sensitive Data
1. Data Masking
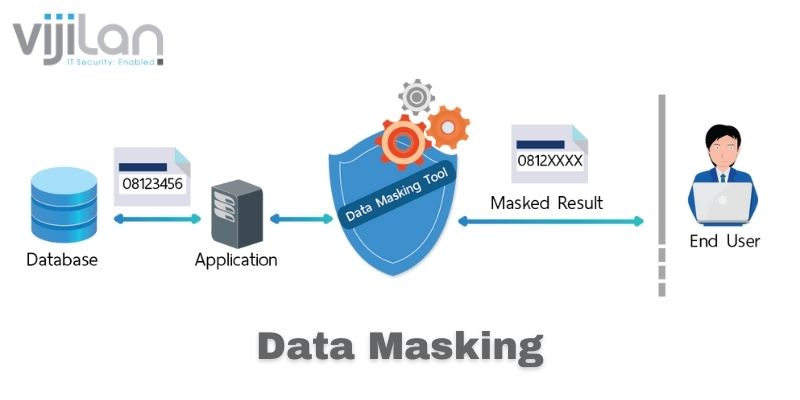
The technique involves the creation of a replica of your company’s data. The replicated dataset will have the same format as the original but altered values. Methods of changing the data are character or word substitution, encryption, and character shuffling.
Data masking creates a version of your organization’s data that can’t be reverse-engineered or deciphered. The replica is used for training and testing purposes instead of the original data. Teams can also develop applications using the replicated dataset.
2. Encryption

This type of data security uses mathematical techniques to secure digital information with a password for its decryption. An algorithm translates the data during the encryption process, making it unreadable. It eliminates the risk of unauthorized access to digital information.
It is necessary to use a secure method for password transfer between the sender and recipient. There are two types of encryption: symmetric and asymmetric encryption. The encryption process is symmetric if the same key or password is used for encryption and decryption.
Contrarily, asymmetric encryption involves using separate keys for encryption and decryption processes. The data owner keeps one of the keys, the private key, secret while the authorized recipients share the public key.
Encryption is an ideal defense technique for obscuring volumes of sensitive content. Only the private key can decrypt information encrypted with a corresponding public key. As a result, unauthorized users cannot read the scrambled data.
3. Data Erasure
The technique destroys stored digital information. It involves the use of software to overwrite data on storage devices. The information may be on a hard disk drive or digital electronic devices. Using ones and zeros to completely overwrite the stored data across an entire machine destroys the digital information.
4. Redaction of Sensitive Files
Removing sensitive information from a document can protect it from getting into the wrong hands. The sensitive content could be Personally Identifiable Information (PII), which is legally restricted. It could also be content of security concerns like planned projects or operations.
In addition, business plans or intellectual property is commercially sensitive. Data security solutions can stop and block documents leaving an organization but contain sensitive information.
Redaction does not alter the actual information stored in the database. Such a security check can delay time-sensitive documents. Fortunately, removing valuable data allows redacted files to continue their journey without delay.
5. Data Resiliency
Challenges like power shortages, hardware problems, data center corruption, or even a natural disaster can affect data availability. Resiliency is the ability to recover data when its availability is compromised. The speed of recovery from a failure is critical in minimizing its impact.
Data security technologies and solutions can help secure computing environments. Your cybersecurity team can track access to stored data with robust security tools. The unit can also block suspicious file movements or high-risk activities.
Impact of Data Breaches
Data has become the bedrock of organizations. Its loss or theft disrupts business operations and poses a risk of insolvency to the affected company. A data breach can have the following effects on a company.
A. Ruins Reputation
People trust organizations to keep their sensitive data safe. A data breach can prompt them to lose confidence in the affected company. As a result, the victim of a cyber-attack loses the loyalty of its customer. Such a situation will hurt the returns and growth of the business.
B. Financial Loss
Cyber-attacks can halt business operations. Victims are likely to record losses during such a period. They may pay ransom to recover their data or access it. Besides, they will have to pay legal fees and fines, repay customers, and even pay for auditing services.
C. Job Loss
Some employees may bear the consequences of a data breach. The individuals are likely to lose their jobs, especially if the attackers exploit their vulnerabilities. Besides, it may be their responsibility to secure the leaked or stolen data.
Data protection solutions can help secure digital information. The numerous connections on corporate networks and endpoint devices to carry data around increase the surface attack exposure. Companies need to monitor their sensitive data and its usage to prevent cyber threats. Besides, failure to comply with data protection regulations attracts fines.
Conclusion
Data security is no longer an option but a necessity. Organizations need to implement the proper data protection solution to prevent data theft or leaks. If you secure your organization’s sensitive information, you will retain its integrity and keep it out of reach of your competitors. Besides, your company will not experience disruptions or financial loss resulting from data breaches. Whether you are a small, mid-sized, or large business at Vijilan, we have the security solutions your company requires. Our extensive systems, technologies, and experienced staff ensure that your network security needs are met. Schedule a free demo with our security experts to know more about how we can safeguard your company’s data and systems.








