Security Operations Center (SOC) is generally known as a 24/7 cyber security operations center. It is said to be an important part of a useful cybersecurity technique. But, it can be very intricate and expensive to carry out SOC operations or set a current SOC out of the reach of several organizations. This implies that it will take a long time before a SOC becomes operational where the cost is on the high side.
Security Operations Center has many benefits even though many business owners have to spend a large amount and put in their best efforts. Companies that turn to SOC services are increasing daily, as they can easily carry out important security functions, such as daily threat detection and response. Here are what SOC entails and its benefits.
What is Security Operations Center?
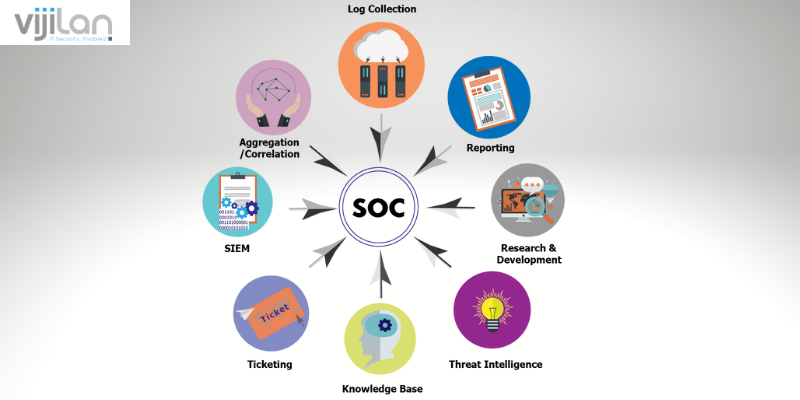
Security Operation Center (SOC) is an area that concentrates on key roles within a company employing people, sets of procedures, and technology to constantly monitor and enhance the security stability of an organization while detecting, responding, preventing, and analyzing cyber security activities.
A Security Operations Center stays in the middle, to take automatic recordings from the IT infrastructure of a company, which includes appliances, networks, information storage, and devices, in whatever location they are found. The amplification of improved threats creates a high placement on text collection from several sources. Most importantly, the SOC is a centralized area for all logged activities, monitored. Therefore, for each logged-in activity, the SOC must determine its management and method of action.
How Does a SOC Work?

The main purpose of a SOC is the implementation of security monitoring and notifications. This is inclusive of collecting and ascertaining information, identifying questionable network events, and enhancing the company’s security system. Threat information is gotten from intrusion detection and prevention systems, threat intel, firewalls, security information and event management (SIEM), and threat intel systems. Immediately there is a sign of abnormality, the SOC team receives a notification.
What Does a SOC Do?
Asset Discovery
SOC makes it possible for assets to be screened for security events, by securing a profound awareness of all software, hardware technologies, and devices used in the company.
Behavioral Monitoring
The SOC examines technology infrastructure around the clock and throughout the year, for irregularities. It also makes use of proactive and reactive measures, to make sure abnormal events are detected and eliminated on time. Behavioral monitoring of questionable cyber security events is implemented to limit lease positives.
Managing Activity Logs
All communications and logged events, that take place within and outside an organization, must be carried out by the SOC team. Incident logs paves way for the SOC to take a step back, and identify past events that may have led to security compromise. Maintaining activity logs can also help reconstruct a point of reference for normal events.
Alert Ranking
Where severe alert ranking is assigned, it helps the SOC team to get the first highest notifications. Security incidents detect and respond to alerts. However, they are not designed in the same way, which is why some, will be assumed as a high risk to a company, than others.
Incident Response
Immediately there are notifications or detections of a data breach, or any other network security compromise, the SOC team is always on the go to carry out significant security duties or perform incident response.
Root Cause Investigation
After a security event has occurred, the SOC team can be made to carry out a thorough examination to find out when, why, and how an event occurred. While the investigation is taking place, the SOC depends on log details to trace the origin of the problem, and use the information to prevent the return of such problems.
Compliance Management
The SOC team is required to carry out operations regarding the company’s policies, regulatory requirements, and industry standards.
What Are the Benefits of Security Operations Center?
Centralized Visibility
Many business networks have encountered more complex growth in today’s digital era. The transformation approach has sent out the implementation of the Internet of Things (IoT), and cloud computing devices while the Bring Your Own Devices (BYOD), and growth of inaccessible work principles encourage the connection of mobile and remote devices to collective networks.
Therefore, managing proper security and visibility toward the business network has become very difficult. This means, that technologies that can be easily implemented on one platform, may hardly be useful on another platform. Also, current technologies have additional and special security requirements and susceptibilities that demand current security solutions.
Cybersecurity Cost is Reduced
It can be very expensive to manage a strong cybersecurity operation. Some organizations may need several licenses and platforms before they can accomplish protection and clarity against network threats. Centralized SOC allows companies to minimize costs by distributing them across the company. Deleting a departmental database system brings about the reduction of an added cost, associated with the process of duplication.
Better Collaboration
Effective collaboration is important for good security incident detection and threat response. Where a company lacks clarity in executing a task, or in identifying, responding, and reporting to a network security event, then the delay that follows raises the probability that a cyber attacker can successfully carry out an objective, and this makes it complex to eliminate the damage completely
Other benefits of Security Operations Center include;
- Uninterrupted analysis and monitoring of system activity
- Reduced schedule of activities between when a network security breach happens and the time of its detection.
- Enhanced incident response.
- Reduced downtime.
- Significant transparency and control across security functions.
- Both customers and employees give their full trust to the company, which is why they can share their sensitive information with ease.
Conclusion
SOC is relevant in improving your ability to pinpoint, monitor, and respond to cyber threats, faced by your organization around the clock and throughout the year. It is important to identify with this command center, which consists of processes, technology, and trained security resources, that are consistently monitoring for harmful actions while also looking out to detect, prevent, and respond to such actions.








