Over time, the incidence of cybercrime has affected several tech companies around the world, and this has caused the loss of useful data in business and individual situations. Luckily, there are updated ways by which an individual can guard against cyber-attacks and check the damages caused by the Attack.
There are several ways to mitigate cybercrime, and using proxy servers is one of those ways. This is how proxy servers can be used to protect against cybersecurity threats:
What is a Proxy Server?
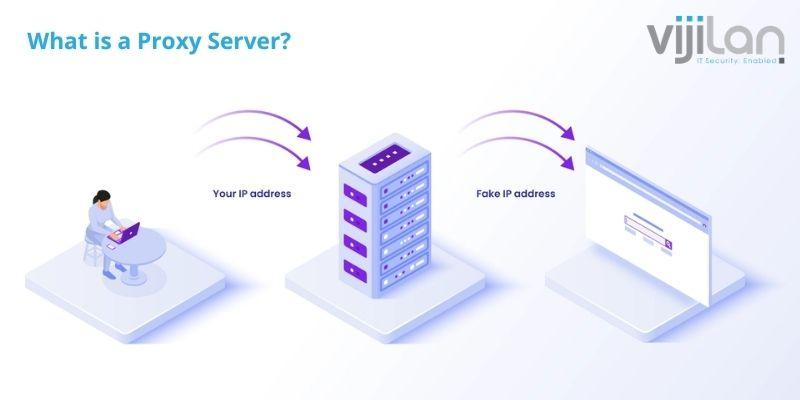
A proxy server acts as an intermediate tool, occurring in reality or virtually, where all internet networks from a web server or computer device travels through. The proxy designates a request from your computer device, where it is addressed in a new IP and left unidentified in the software browser.
With proxy servers, you can guard your identity even when exposed to internet fraud cases where cyberattacks implicate identity theft. In general, cybersecurity proxies are used in multiple applications.
Types of Proxy Servers
Many types of proxy can be used to protect your computer, depending on what you need and your privacy requirement. Proxy servers can be generally divided into:
Anonymous Proxy Servers:
When you use an anonymous proxy, a fake IP address will be provided by the proxy instead of your actual address. Websites can ascertain your IP address to find out whether you are using a proxy server, but your primary IP address will not be known.
High Anonymity Proxy Servers:
An unidentified IP address including an anonymous proxy added with privacy settings can completely conceal your proxy use.
Transparent Proxy Servers:
These types of proxies do not help you hide your IP address identity, and this implies that there may be no provision of privacy or security. Instead, these proxies are usually used with the aim of filtering contents. Transparent proxies are commonly used in offices and schools.
Why Is it Important to Use Proxy Servers for Cybersecurity?
To Protect Against Email Phishing
Email phishing refers to a form of cyber violation where criminals assume an organization’s identity using text messages or emails.
These cybercriminals act intending to do away with essential credentials or money from the victim’s account. Furthermore, email phishing can similarly lead to ransomware or malware attacks, which can prompt the loss of millions of dollars.
Organizations can forestall situations like this by using intermediary servers. Proxies for email assurance make an easy and seamless scratching that searches mail for harmful connections or contents.
For this, dangerous messages are checked out of inboxes. Also, note that datacenter proxies should be liked for this task area due to their speed, uptime, and Superior Performance.
Aside from using proxies, organizations can also invest in sufficient ransomware coverage. Companies ready to work with their network security can do so by checking their occurrence response plans with significant ransomware workouts. Our ransomware accessibility checklist is a good place to begin.
To Identity Theft/ Brand Protection
Duplicating is a problem that can lead to loss of income. Many organizations can suffer up to billions of revenue losses. Those guilty of this crime embrace brand or wholesale theft. They start by producing counterfeit items, which they package, using certifiable trademarks of known companies.
At the end of the process, the fraudsters sell the fake items as though they were genuine through online companies or physical stores. The good news is that some business organizations can screen listings of such products through intermediary servers.
In general, proxies give permissions to geographically-hindered sites. Indeed, it is a way for proxy service providers to have a vast pool of IP addresses.
The vast pools often contain IP addresses from various geographical areas. All things being equal, intermediary servers allow companies to access content intended to be shown to inhabitants of particular nations.
To Stop Distributed Denial of Service (DDoS) Attacks
A DDoS attack is a harmful attempt to disrupt the operations of a functioning website. An attacker begins by sending a massive number of message requests. The server can hardly resist these requests, as they are often overwhelming.
To stop attacks done on DDoS, organizations should utilize a content delivery network (CDN). A CDN is an organization of proxy servers conveyed in different regions. Each proxy inside the CDN has the site’s substance.
Simultaneously, reverse proxies can put a stop to DDoS attacks. Switch proxies are designated on the server’s internet association. This keeps the server away from attacks by keeping away consistently accessed website pages in retrievable storage. It is designed by operating the server as the need arises.
For Malware Protection
Over Time, many companies have used transparent intermediaries to block sites containing malware. This intermediary form makes it easy for users to link with secure websites. As a result, users will hardly perceive their existence in a networking system.
To Prevent Data Breaches and Attacks
To an extent, phishing goes beyond emails. Cybercriminals typically create their scam phishing sites that have a similar URL business appearance. According to reports, 611,877 phishing websites were documented in data in Q1 2021, leading to 269% when it was matched with the Q1 2020 report.
The purpose of such a site is to achieve credentials from anonymous users. However, organizations can take on website scratching to point out and prevent the operations of phishing sites, using fast and influencing data center proxies.
Conclusion
Proxy servers offer an additional layer of protection to ward off Internet fraud and scams. It is crucial to note that you can use many types of intermediary servers for your cybersecurity functions.
Proxies like datacenter types are recommended because they have unique speed, high performance, and high uptime characteristics. Also, you can use both transparent and reverse proxies to protect your network or server against malware and DDoS attacks. Book a free demo today to know more about Vijilan‘s comprehensive cyber security solutions and benefits.








